Atomic Red Team
Introduction
Atomic Red Team is an open-source project that provides a framework for performing security testing and threat emulation. The main goal of Atomic Red Team is to ease the threat emulation process. Atomic Red Team’s tests are mapped to the MITRE ATT&CK framework.
Every Atomic Test is written for a specific MITRE Technique where the files are named as its mapped MITRE Technique ID. We can find the collection of available tests here.
Set up
First we’ll need to open PowerShell as an administrator. Secondly, we’ll set the ExecutionPolicy to bypass in order to ignore the security warning prompts for the module.
powershell -ExecutionPolicy bypassThird, we’ll import the module using the following command.
Import-Module "path/to/file/Invoke-AtomicRedteam.psd1" -ForceNext, we’ll need to update the PSDefaultParameterValues var
$PSDefaultParameterValues = @{"Invoke-AtomicTest:PathToAtomicsFolder"="C:\Tools\AtomicRedTeam\atomics"}Once that is imported, we can then check to see if it’s working by using the help command.
help Invoke-AtomicTestUsage
We can list the available atomic techniques. For example if we wanted to see if T1123 is available.
Invoke-AtomicTest T1123 -ShowDetails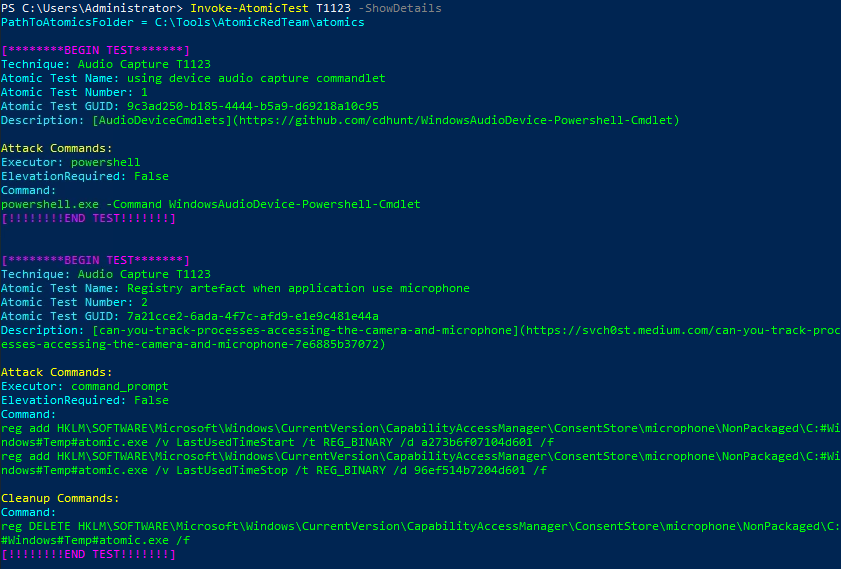
The output above gives us the attack commands that it’ll run as well as the clean up commands.
Prerequisites
Some techniques will have a Dependencies section. In order to check with the pre-requisites are met, we can run the following command with the technique we want to use.
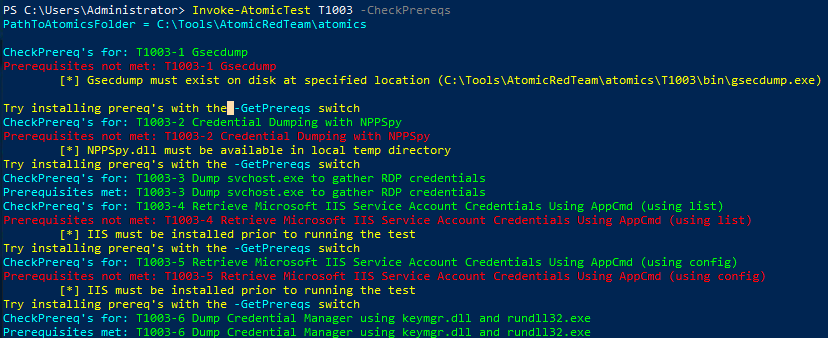
We can then try to pull the dependencies from an external source using the following command.
Execution
There are multiple ways of executing the Atomic tests.
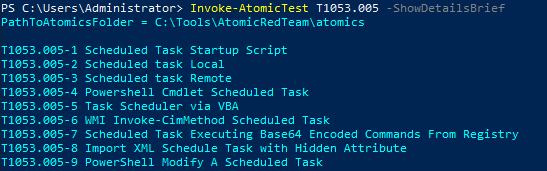
If we look at the screenshot above, we can execute these tests in multiple ways. The first way would be with the TestNumbers which runs the tests by the numbers that we see to the right of T1053.005.
The next way of executing tests is by the test name which is everything to the right of T1053.005–1.
Alternatively, we can execute all tests or just a single test.
We can pass in custom arguments into each test through the command line by using the -PromptForInputArgs flag when we run the command.
Cleanup
After executing any of the tests, it’s very important to clean up the results of those emulations. Atomic Red Team offers a Cleanup parameter that we can use to clean up the effects of the test.
Adding New Atomic Tests
In some cases Atomic Red Team may not have the corresponding Atomic or test for the the MITRE techniques that you’re looking for.
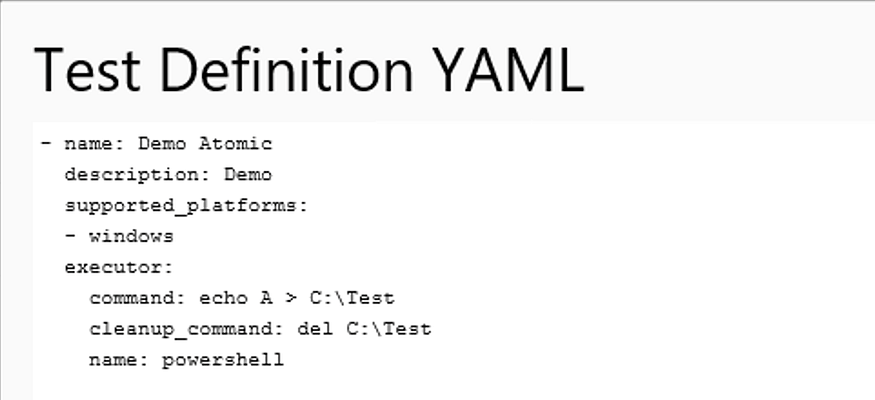
We can create new tests using the Atomic Red Team GUI.
Once that’s started, we can then visit it at localhost:8487/home in the browser.
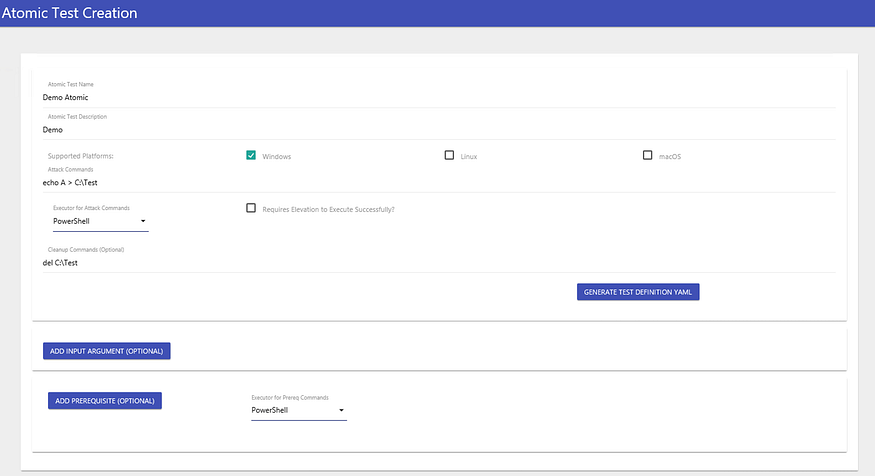
We can then fill out the form and generate the YAML file by clicking on the Generate Test Definition YAML button.
REFERENCES
Last updated