🐋docker container escape
Theory
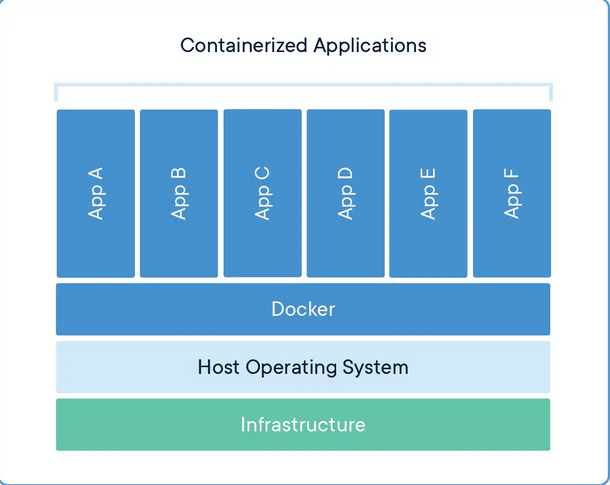
Practical (Exploitation)
Checking if we're in Container
Docker Escaping Techniques
1. Escape via Exposed Docker Daemon
2. Shared Namespaces
3. Escape By Mounting File System
4. Misconfigured Privileges
5. Exploitation of docker.sock in /var/run or /run if you're ROOT
6. Debugfs
3. Writeable Backup Scripts
REFERENCES
Last updated